Delhi: Ransomware these days needs no introduction. The perpetrators behind ransomware have done more than enough damage to critical infrastructures and collected billions of dollars from victims across the world and are still collecting. Ransomware attacks have become highly targeted and aimed at large enterprises. Ransomware actors preferred to perform targeted and highly lucrative attacks – with ransom demands from successful attacks reaching millions of dollars. Also, ransomware actors started threatening to leak data of attacked organizations uncooperative in paying the ransom.
The ransomware landscape has evolved into a massive problem in the past few years. The modus operandi and Tools, Tactics, and Procedures are more mature, threat actors are targeting big public and private organizations and the amount of the average ransom payments have increased significantly as well. The arrival of Bitcoin and alternative cryptocurrencies gave a real boost to the viability – and profitability – of ransomware. Threat actors could now rely on a permission-less payment system to execute the transaction.
Col. Inderjeet explains in detail what is Ransomware and the type of variants. Ransomware is popularly described as a type of malware that makes a file on a victim’s computer or device inaccessible and then demands the victim to pay ransom mostly in the form of bitcoin or other means of payment to regain access to the hijacked system. Experts popularly describe ransomware as scareware that makes data and resources on a victims’ computers inaccessible and forces the victims to pay a ransom with bitcoins or through other means by frightening and intimidating them.
Hackers and people with malicious intent are responsible for spreading ransomware. However, we know from experience that employees also contribute to the spread due to human error and or ignorance caused by lack of awareness. Some of the conventional methods of spreading ransomware include exploiting systems known or unknown vulnerabilities or by visiting compromised sites or deep webs.
Also Read: Ransomware feared as possible saboteur for November election
The New Age of Ransomware emerged in 2013. Threat actors began employing a vast, shadowy infrastructure to execute attacks and process payments. Cryptolocker was the first large-scale ransomware operation, targeting around half a million computers and collecting a total of $27 million in ransoms.
The sudden rise of ransomware attacks recently is a signal that ransomware has come back with full force in both complexity, impact and size. The year 2017 was the year, history will never forget as per as internet security breach is concerned. It was the year in which the world saw some of the most dangerous attacks in history including the WannaCry pandemic, Petya, NotPetya, Cerber, Cryptomix, Locky, CrySis and many others.
The year 2020 has seen a phenomenal rise in Ransomware attacks with a large number of variants such as Revil, Sodinokibi, Nemty, Nephilim, NetWalker, DoppelPaymer, Ryuk, Maze, CLOP, Tycoon, Sekhmet, Lockybot, and many more.
These aforementioned ransomware attacks were massive global ransomware attacks that mostly affect Windows Operating Systems that were unpatched or unsecured. We must undoubtedly accept the fact that the year 2017 and 2020 have seen what many will call the ‘fall of security infrastructure’. So far we must say that modern technologies have failed woefully and proved insufficient and inefficient in the fight against ransomware.
Col. Inderjeet, " The damages erupted by ransomware did not catch much attention until recently when hundreds of companies and security agencies across the world have begun to cry out. A popular variant known as WannaCry had rapidly spread to around 200,000 to 300,000 machines in over 150 countries across the globe since its first appearance. Garmin Company recently was hit by a ransomware attack in the month of Jul 2020."
Previous ransomware attacks used a ‘spray-and-pray’ approach, attacking as many machines as possible in massive phishing campaigns, hoping many would be compromised. They asked for a ransom of a few hundred dollars’ worths of cryptocurrency. This has changed. Campaigns now are more targeted, and the ransom amounts have increased sharply. The average ransom paid is now $36,295 and for the public sector, the average sum is $338,700. This trend shows no sign of abating. The extremely high return on investment for threat actors (and aspiring threat actors) is too good to resist.
Also Read: How Fake News can be Stopped using Blockchain?
The rise of crypto-ransomware has led to the reinvention of even more sophisticated and well-enhanced ransomware. Hackers started designing exploit kits that were used for creating other series of ransomware variants. Since the emergence of ransomware, new variants of ransomware are being released every day. Perhaps it is important to note that, types of ransomware should not be mistaken with variants of ransomware, the variants are the distinctive types of ransomware family which possess unique features and patterns of operating. In tracing the different variants of ransomware family, one might say they are infinite.
Col. Inderjeet further adds, "The question many people keep asking is why is ransomware prevalent and unbeatable in every part of the world? The reason is that antivirus and anti-malware are no longer capable of detecting ransomware because modern ransomware use polymorphism and machine learning to avoid being detected. Secondly, the advent of Ransomware as a Service and the Exploit kits as a service in black markets make it even more difficult to deal with the situation. With Ransomware as a Service (RaaS), anyone including script kiddies can lay their hands on ransomware codes and reproduce their own."
Ransomware as a Service (RaaS) is a fee-based model. The threat actor does not execute the cyberattacks: it develops and rents out the ransomware and its underlying infrastructure. The sale takes place on hacking sites on the clear web and the dark web. By paying a monthly fee, anyone can buy ransomware, along with associated patches, enhancements, and support. In addition to the license, the malicious actor will also have to share a percentage of the ransom money with the RaaS operator.
Also Read: Dark Side of Artificial Intelligence
Targeting multiple other sectors ranging from IT, media, energy, retail, real estate, legal, transportation, healthcare, manufacturing, entertainment, non-profit, and the government is a new trend for ransomware operations in 2019 and 2020. Many municipalities and counties, particularly in the US, suffered ransomware attacks that brought their operations to a complete halt, with the exception of emergency operations, such as police and firefighters, which normally operate on separate networks.
As we can see from looking at these cases, recovery costs can outweigh ransom costs by orders of magnitude, often by paying the ransom in the most preferred options. This is the case for many local governments whose disaster recovery processes may be lacking. In many cases, these organizations have taken insurance covering cyber incidents. Such insurances make payment of the ransom,a highly likely and preferable option.
Eighty-five percent of managed service providers (MSPs) say the Windows OS is targeted most frequently by ransomware attacks. The reason? Windows-based computers are typically more affordable, therefore more people use them. There are also enough people who use them that don’t install necessary updates for their operating systems, leaving them without patches that protect against these viruses. This makes them an easy target for online bad actors. Popular software as a service (SaaS) applications are being targeted by ransomware, too. A study involving several multiple service providers found that Dropbox, Office 365, G Suite, Box, and Salesforce have experienced ransomware attacks in some form.
One of the Survey provides fresh new insights into the experiences of organizations hit by ransomware, including:
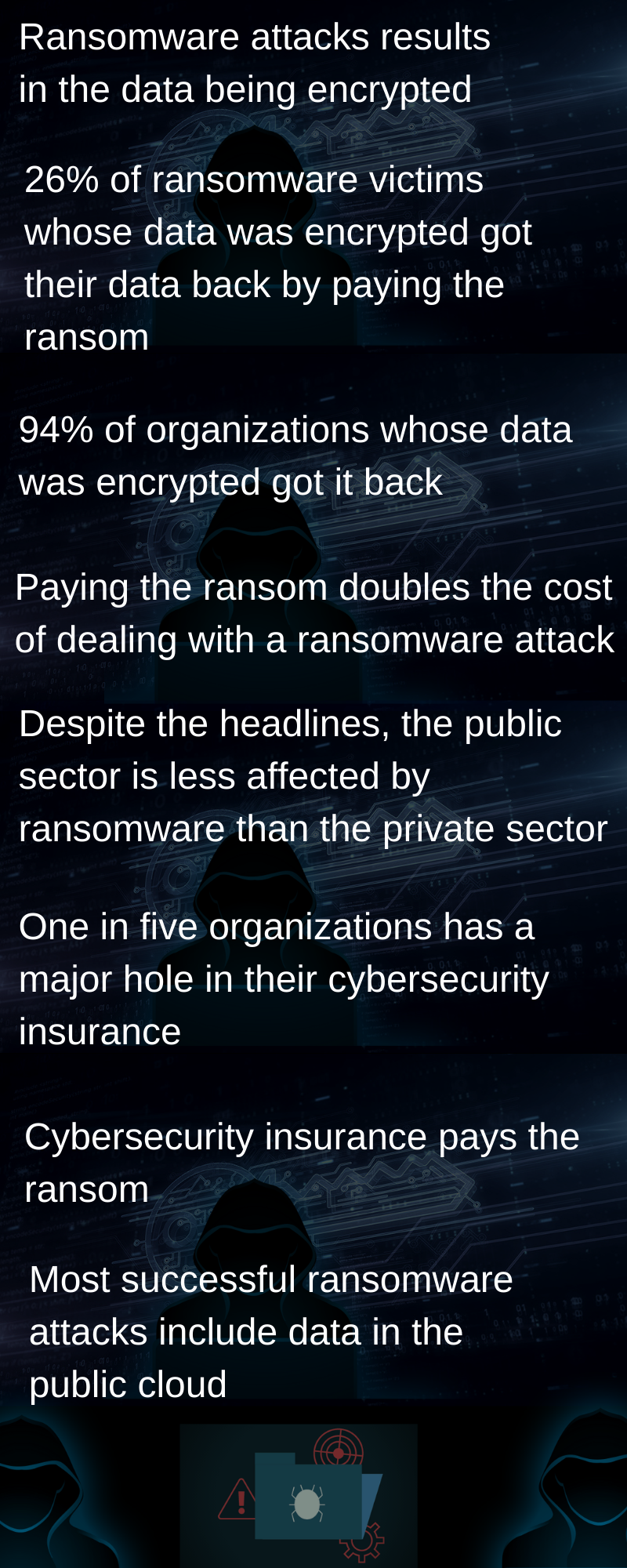
- Ransomware attacks result in the data being encrypted. 51% of organizations were hit by ransomware in the last year. The criminals succeeded in encrypting the data in 73% of these attacks.
- 26% of ransomware victims whose data was encrypted got their data back by paying the ransom. However, 1% paid the ransom but didn’t get their data back.
- 94% of organizations whose data was encrypted got it back. More than twice as many got it back via backups (56%) than by paying the ransom (26%).
- Paying the ransom doubles the cost of dealing with a ransomware attack.
- Despite the headlines, the public sector is less affected by ransomware than the private sector.
- One in five organizations has a major hole in their cybersecurity insurance.
- Cybersecurity insurance pays the ransom. For those organizations that have insurance against ransomware, 94% of the time when the ransom is paid to get the data back, it’s the insurance company that pays.
- Most successful ransomware attacks include data in the public cloud. 59% of attacks, where the data was encrypted involved data in the public cloud.
Ransomware isn’t going away any time soon. Data loss is a serious concern that affects both individuals and companies. Quite simply, it works, so individual users and businesses will continue to be targeted. URLs embedded in emails remain the number one way for computers to become infected.
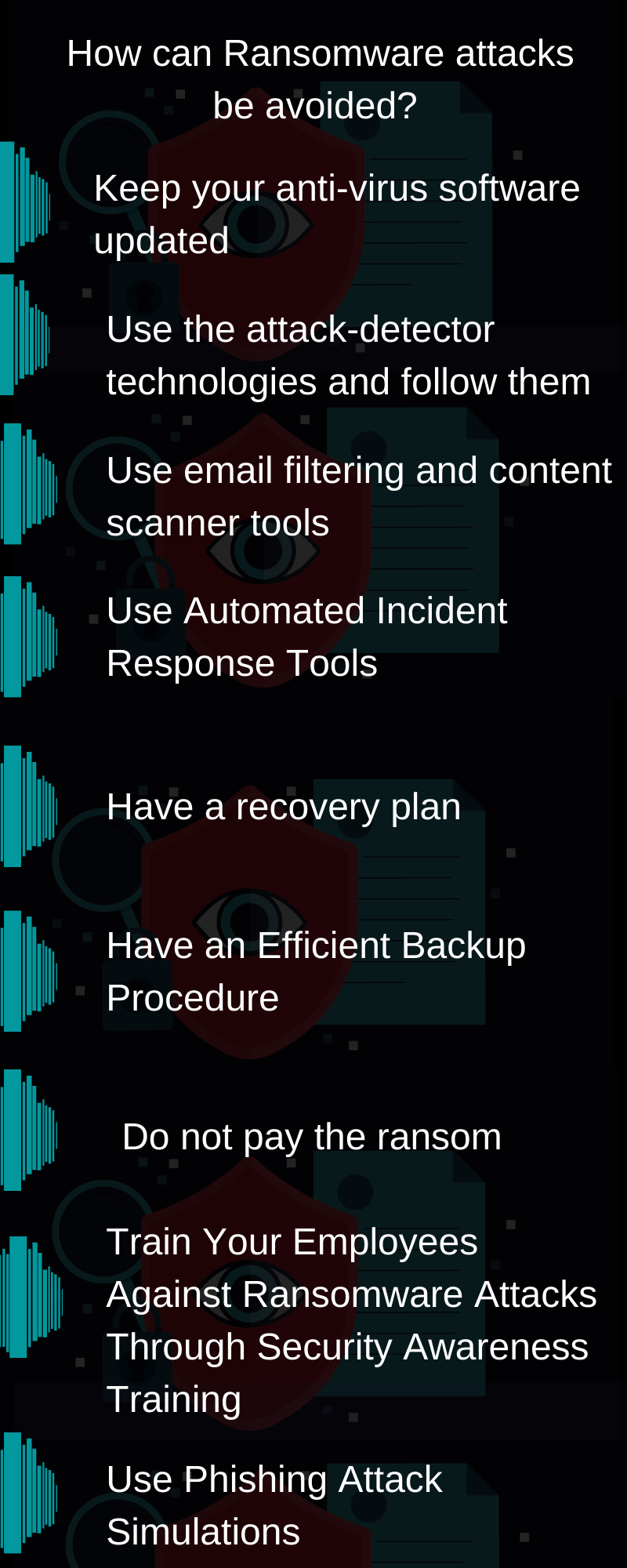 ways ransomware attacks can be avoided
ways ransomware attacks can be avoided

What Should You Do During A Ransomware Attack?
If you are attacked by ransomware, there are 4 steps to follow:
- Close all file-sharing activity in your device if you notice any ransomware infection.
- Evaluate the virus and the damage caused by it. If needed, find the encrypted files with the help of antivirus software.
- Clean all infected ones.
- Recover the infected files by backing them up with the help of a cloud system.
You can follow Col. Inderjeet on twitter @inderbarara, insta:inderbarara
Also Read: Insight into Twitter hacks using Bitcoin Scam by Col. Inderjeet Singh, DG, CSAI



