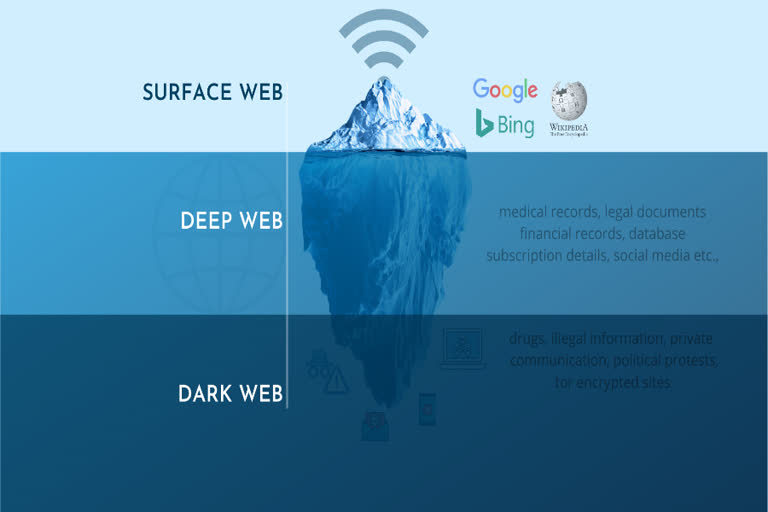
Delhi: For many individuals, the Internet appears as an endless virtual world of global e-commerce and information. Goods can be purchased and delivered to your doorstep, information can be accessed at the swipe of a finger and dreams come true. Their web activity is limited to about twenty to fifty websites, with most of it being Google-related sites and services. Similar to the explorer submarines, the search engines scour the internet and display what they find to users.
Col. Inderjeet Singh, Cybersecurity Expert, Director General, Cyber Security Association of India said that while the internet appears to be a flat ecosystem on its surface, there are actually numerous different layers at play. In reality, there are three (3) major areas of the Internet to differentiate between:
- The Surface Web,
- The Deep Web, and
- The Dark Web.
When on the topic of the Dark Web, the Deep Web may be thrown in or used interchangeably, but the two different internet layers vary quite a bit, especially with regards to the content. But the internet has a dangerous, colossal secret: the Dark Web.
The term Dark Web and its synonyms such as Darknet, Onionland, the Other Internet, and others have been getting a lot of press these days. Constant reports of data breaches, identity theft, and state-sponsored hacking fill our daily headlines. Although many people have heard the terms, few actually understand what it means.
Also Read: Protecting Critical Infrastructure from Cyber Attacks
The deep web is presumably 100 times larger than what is known as the “surface web” which is what you and I surf through search engines like Google, Yahoo! and Bing. Most of the deep web isn’t evil in any way, it’s just content blocked from search engines for security reasons. There are some deep web search engines that let you explore some of them.
The deep web comprises mostly legal content that is not listed on search engines and requires special permissions to access such as bank records, password-protected pages, encrypted chat records, email correspondence, paid streaming services, and many more.
But here’s the interesting part of the deep web: The Darknet. A part of the internet that isn’t accessible through search engines at all, and also much more. It’s an anonymous Internet. On the Darknet, no one knows your identity and no one knows who is behind any website.
This is where people go to look for stuff when they don’t want to be found. Darknet isn’t all evil. A large part of it is just normal forums, blogs, essays, etc. Because of the protection offered by the Darknet and its hidden services, activists in oppressive regimes are free to exchange ideas and organize themselves and then there’s the bad stuff – contract killers, child porn, drugs, and other nasty stuff that share the same benefits of anonymity as the good sites.
What Types of Content Can Be Found on the Dark Web?A wide variety of content can be found on the deep web. Some of the broad categories of content that may be found there include:
- To visit the dark web you need to install a specialized browser that anonymizes your network connections, such as Tor or I2P.
- The Tor browsers allow you to route your web page requests via a series of proxy servers, hiding your IP address and making your connection untraceable.
- However, while Tor serves to mask your identity, using it to access the dark web can be slow, unpredictable, and at times unreliable.
- Dark websites have a different naming structure from those of regular sites.
- While regular sites end with .com or .co, dark websites end with .onion. The special suffix designates an anonymous hidden service, accessible through the Tor network. Only dark web browsers with the appropriate proxy can reach these sites.
- Darknet uses layered encryption and does not use Domain Name Servers (DNS) or IP addresses. This makes it difficult to track the identity and locations of users, as their data routes through a large number of servers. Essentially, a user’s communications bounce around to different servers around the world to help keep them private.
Also Read:Artificial Intelligence in Cyber Warfare
Col. Inderjeet further explains," Just as the users can purchase products through sources such as Amazon and eBay on the Surface Web, Tor users can purchase illegal products or services through Dark Web counterparts. There are many different markets available on the Dark Web selling variety of stolen and illegal products, including weapons, drugs, and stolen information."
There are also more specialized markets to purchase cybercrime services, showing us why cybercriminal activity is so common. These nearly-anonymous cybercrime markets make it much easier for less experienced cybercriminals to distribute malware or target businesses. Some of the products and services readily available include:
One of the most frequently asked questions about the Dark Web is: “do these guys ever get caught?” It is difficult for authorities to take down Dark Web sites due to a number of factors, including Tor’s multi-layered encryption, criminals using anonymous VPNs, sites being hosted in different countries (without strong cyber-laws), and the use of bitcoin or another cryptocurrency (nearly untraceable) when purchasing illegal good or services, rather than transacting through a Bank.